Do you have SharePoint installed on a development or test environment somewhere? Does it have it’s own Active Directory installation? So, how do you explore all the wonderful features of the SharePoint User Profile service? You know, like the Silverlight organisation chart, or Audiences, or Colleagues, or…
Well, not to fear, after much procrastination, I’m finally able to provide a solution to your problem. I’ve made up names, job titles and managers for 100 people. Any similarity to real people is purely coincidental. Not only that, but I’ve created a PowerShell script to create these accounts in Active Directory.
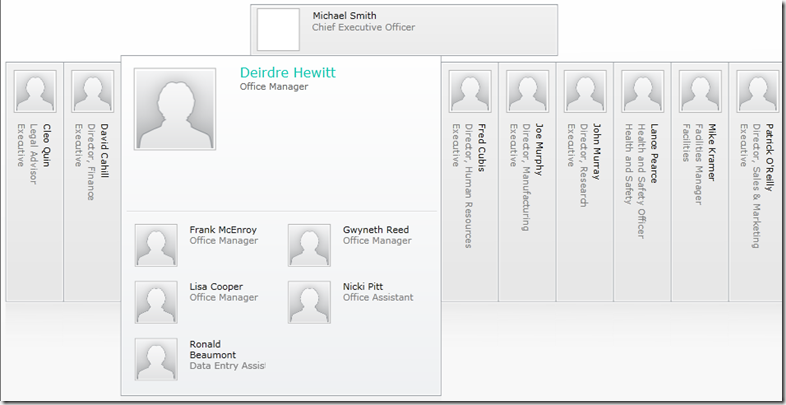
This means your User Profiles in your virtual environment can go from a bland handful of test accounts, to a dazzling collection of fictitious employees in different departments, physical offices and job titles. Just imagine the Audiences you can create!
Feel free to edit the CSV file (using Excel) to modify personal details and add more people. You can even add additional user properties, but you will also need to make some changes to the PowerShell script to get these into Active Directory, not hard if you are familiar with PowerShell.
I’ve tested the PowerShell script on a Windows 2008 R2 domain, however I executed it from a Windows 7 desktop. The script does not require Microsoft Exchange or third party script add-ons. I execute the script using the domain admin account. You may run into issues if you try using accounts with less privileges.
The script contains a path to an Active Directory Organisation Unit (OU) where all the accounts will be created (OU=Staff,DC=lab,DC=laptop,DC=iw). You will want to change this before running it in your environment. This OU needs to exist before you run the script.
I have configured the script to create the accounts but not to enable them. This is for security purposes. However, if you want to enable them, you just need to uncomment two lines and seek legal advice.
You can download the zip file containing the people details and PowerShell script from here. Any feedback greatly appreciated.
